Network-Level DMZ Connectivity Architecture
This section provides information for network engineering teams responsible for the deployment of event borkers (specifically Solace Appliance Event Brokers) in the DMZ to provide high-availability connectivity into the underlying Layer 2 switch infrastructure.
If there is no requirement for physical separation between internally-facing subnets and externally-facing subnets within the DMZ, then the typical Solace network connectivity options can be used, that is, a Link Aggregation Group (LAG) for 1GE connectivity or port bonding for 10GE connectivity.
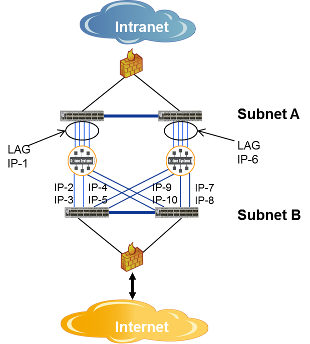
In cases where physical separation between subnets within the DMZ is required, more care must be taken. This figure shows a typical deployment using an 8x1GE NAB to provide redundancy on both the intranet-facing (that is, internal) and internet-facing (that is, external) sides. In this case, a LAG is used to provide port and link redundancy facing the intranet, while individual IP interfaces (one per port) are used facing the internet. Typically, the external firewall (for example, BigIP device from F5) monitors the availability of each internet-facing IP interface and then load balances incoming HTTP requests to available IP interfaces based on URLs (as discussed in Session Load Balancing to Event Brokers Within a DMZ).
In deployments using a 2x10GE NAB on the Solace Appliance Event Broker, one port is connected to the subnet facing the intranet, while the other port is connected to the subnet facing the internet. Thus, there is no port or link redundancy.
Active/Active redundancy on Solace Appliance Event Brokers is typically not used the DMZ since the URL with appliance event brokers in routing rules of the external firewall, combined with the ability of the firewall to monitor the status of Solace interfaces, allows for an N:1 resiliency model, whereby the load from one failed appliance event broker can either be switched to another spare or standby appliance event broker, or spread among existing appliance event brokers, thereby providing more cost-effectiveness with high availability.