Management User Authentication / Authorization Overview
There are two ways you can authenticate users to provide management access to a Solace event broker: Basic Authentication or OAuth Authentication.
Basic Authentication
When setting up basic authentication, there are two types of management users that can connect to an event broker:
- CLI user: A user that connects to an event broker for the purpose of configuring, managing, and monitoring that event broker. A CLI user can be an administrator that uses the Solace Event Broker CLI (CLI) or Broker Manager (a browser-based administration console), or SolAdmin(a GUI-based equivalent of the Solace Event Broker CLI). It can also be a management application that uses Solace Element Management Protocol (SEMP) request over HTTP service. (For information on SEMP service, see SEMP.)
- File Transfer user: A user that can remotely transfer files to and from specific directories on the selected event broker using Secure File Transfer Protocol (SFTP) or Secure Copy (SCP).
When a user successfully logs in or logs out, or fails to authenticate for a Solace Event Broker CLI, SEMP, shell, scp, or sftp session to the event broker, an authentication event is written to the event log. If SEMP is used to manage the event broker, a persistent SEMP connection should be used if a high volume of authentication event logs is not desired.
OAuth 2.0 Authentication
There are two ways you can use OAuth to provide management access to an event broker:
- Interactive: OAuth is used to authenticate a user interacting with Broker Manager or any other browser-based web application that use SEMPv2.
- Automated: OAuth token is used as credentials to authenticate REST request from SEMPv2.
Basic Authentication
When a Solace Event Broker CLI user initially establishes a connection to the event broker, no requests by that user can be processed until it is authenticated according to the authentication type that has been configured for that CLI user account.
The following authentication types can be configured for a provisioned CLI user account:
- Internal—The CLI user’s name and password are authenticated against an internal event broker database.
- RADIUS—The CLI user’s name and password are sent to an external RADIUS server for authentication.
- LDAP—The CLI user’s name and password are sent to an external LDAP server for authentication. LDAP over TLS is also supported.
The event broker always first attempts to authenticate a CLI user using internal authentication. If user does not exist in the internal database, the event broker checks if either RADIUS or LDAP authentication is configured (one of the two can be configured for the event broker). If RADIUS or LDAP authentication is configured, the event broker then attempts to authenticate the user using one of those authentication types. For information on how to configure RADIUS or LDAP authentication, see Setting CLI User Authentication Types.
If the CLI user is successfully authenticated, the event broker permits the connection with the access privileges configured for the CLI user account.
If you are using RADIUS or LDAP user authentication, it is recommended that you configure a few internal user accounts that can be used to administer the event broker if the external RADIUS or LDAP servers are unreachable. However, do not duplicate internal user accounts on a RADIUS or LDAP server or vice versa, because this can cause confusion over where user account passwords reside. For example, if a user account password is changed on the RADIUS or LDAP server, and a duplicate account also exists locally on the event broker, internal authentication will be used and because the old password is expected, the user authentication will fail.
File Transfer User Authentication
A file transfer user is authenticated through the Internal authentication type. The File Transfer user’s name and password are verified against the internal event broker database. If the verification is successful, the event broker permits the connection.
File Transfer user accounts do not have a permission level associated with them. All File Transfer users can read, write, and delete files from the file system available to File Transfer users.
OAuth 2.0 Authentication
OAuth allows applications to perform authentication using temporary tokens instead of permanent credentials. Using OAuth, users interacting with Solace event brokers can be authenticated without requiring access to their permanent credentials. Note that OAuth is only supported over TLS.
There are two ways you can use OAuth to provide management access to an event broker:
- Interactive: OAuth is used to authenticate a user interacting with Broker Manager or any other browser-based web application that use SEMPv2.
- Automated: OAuth token is used is as credentials to authenticate REST request from SEMPv2.
When using OAuth to access Broker Manager, the user will be logged in based on the token from a third-party identity provider. If OAuth is configured as the authentication method, an OAuth login button will be displayed on the login screen. Clicking the button will redirect the user to the OAuth identity provider's login page where they can enter their credentials. If the user is already logged with the provider, they will be immediately redirected back to Broker Manager. For more information, see Configuring OAuth Authentication.
Similarly, with the automated setup, when a client makes a SEMP v2 request using OAuth, it will include one or more OAuth tokens in the HTTP Authorization header as a bearer token. The event broker will verify the token and automatically select the correct profile. For more information, see SEMP Authentication and Authorization.
User Access To CLI Commands
Each command offered through the Solace Event Broker CLI has a particular scope and access level requirement. Therefore, a CLI user can only use a command offered through the CLI if that user’s configured access levels are sufficient for the scope of the command.
CLI User Access Levels
Access levels are assigned to each CLI user account to control what types of commands the user is allowed to execute. The following access levels are available:
- none
- read-only
- mesh-manager
- read-write
- admin
The CLI user cannot execute CLI commands except for a few that pertain to the log in and display preferences for the user’s own account.
The CLI user can execute CLI commands to display operational information about the event broker but cannot change its configuration. A monitoring application would typically use a read-only access level.
The CLI user can execute CLI commands to both display operational information about the event broker and perform some event broker configurations—including all aspects related to client connectivity, mesh connectivity, and client security features. This access level is useful for users that need access to these commands, but are not allowed global read-write access. A management user responsible for administering an event mesh would commonly be granted a mesh-manager access level.
The CLI user can execute CLI commands to both display operational information about the event broker and perform most event broker configurations—including creating other CLI user accounts with access levels of none. A management user responsible for configuring the event broker or Message VPN services would commonly be granted a read-write access level.
The CLI user can execute all CLI commands on the event broker. This includes controlling event broker-wide authentication and authorization parameters and creating other admin users. (This access level can only be applied to global-scoped commands.)
CLI Command Scopes
CLI users can be configured to manage the entire event broker and/or a subset of Message VPNs. To permit this level of control, each CLI user account is assigned access levels for the following different scopes:
- global
- Message VPN
A global access level dictates what the user is allowed to do across the entire event broker.
One or more Message VPN access levels dictate what the CLI user is allowed to do within Message VPNs.
An assigned Global access level is all-encompassing and takes precedence over the Message VPN access level. It gives a CLI user the same level of access for all CLI commands, including those that have a Message VPN scope. To configure, see Configuring Global Access Levels.
In addition to a global access level, Message VPN access levels are assigned so that users with none or read-only global access levels can be granted increased access to Message VPN-scoped CLI commands, as required. An assigned Message VPN access level can only increase–not decrease–the Message VPN access level that a CLI user effectively receives from its assigned global access level. The Message VPN access levels can be assigned through:
- The default Message VPN access level
- Message VPN exceptions
This provides a consistent Message VPN access level across all provisioned Message VPNs. A default Message VPN access level is always assigned to a CLI user, but it only affects a CLI user’s access to Message VPN-scoped CLI commands if it is greater than the user’s assigned global access level. For more information, see Configuring Message VPN Default Access Levels
These are per-Message VPN exceptions to the default Message VPN access level. These exceptions can either increase or decrease the assigned default Message VPN access level for the specified Message VPN. For more information, see Configuring Message VPN Access Level Exceptions
Assigning both global-scoped and Message VPN-scoped access levels allows the appropriate access to be granted to users based on their administrative roles. Consider the two following examples:
- A system‑wide administrator could be assigned a global access level of admin, which allows that user to run any command on the event broker, whether it is a global-scoped or Message VPN-scoped command.
- A user who needs to monitor operational statistics within a Message VPN could be assigned a global access level of none and a Message VPN access level of read-only for that Message VPN.
For security reasons, only a few administrators should be given access to CLI user accounts with global access levels of read-write or admin. In general, Message VPN-scoped CLI commands contain the message-vpn keyword, or they are contained in a CLI mode with the message-vpn keyword. For example, commands to configure client usernames, durable endpoints, and Distributed Caches are created on a per-Message VPN basis:
solace(configure)# client-username <username> message-vpn <vpn-name>
solace(configure/client-username)# acl-profile <name>
...
solace(configure)# message-spool message-vpn <vpn-name>
solace(configure/message-spool)# create queue <name>
...
solace(configure)# message-vpn <vpn-name>
solace(configure/message-vpn)# distributed-cache-management
Assigning Access Levels
For information on assigning access levels, refer to Configuring Default CLI User Access Levels with External Authentication.
Creating and Managing CLI User Accounts
Your ability to create and delete user accounts, and to change the access levels and passwords of existing user accounts, depends on the global access level of the user account you use. The general limitations for each global access levels are as follows:
- A CLI user with a global access level of admin can create, delete, or make changes to other CLI user accounts without any restrictions.
- A CLI user account with a global access level of read-write can:
- only create or delete other CLI user accounts with a global access level of none
- set a Message VPN access level for any CLI user account
- change the password for its own user account and user accounts with an access level of none
- A CLI user account with a global access level of mesh-manager, read-only, or none can only change the password of its own user account.
When access level and password changes are made to a CLI user account, they do not affect any active sessions that are using that user account. The changes only take effect the next time a user logs in to that CLI user account.
Access Level Capabilities
There are multiple possible global access levels and Message VPN access levels that can be assigned to a CLI user with various capabilities and limitations.
CLI users only see commands that they are authorized to execute. This means, for example, that Help commands will not show unauthorized commands, and CLI tab‑completion will not complete a command for which the user is not authorized. In addition, wildcard characters used in CLI commands will not allow a user to see or access network resources, such as Message VPNs or client profiles, that they are not authorized for.
Global Access Levels
The table below provides information on the possible global access levels that can be assigned to a CLI user and many of the capabilities and limitations that those access levels present.
| Level | Capabilities and Limitations... |
|---|---|
|
none |
The CLI user has access to minimal CLI commands, and no jail file system access. However, a CLI user with this global access level can:
CLI users with a global access level of none can be given additional access to Message VPN commands by assigning them a default Message VPN access level of read-only or read-write or a Message VPN access level exception of read-only or read-write. |
|
read-only (The default value for the global access level.) |
In addition to the capabilities offered by a global access level of none, a CLI user with a global access level of read-only can:
CLI users with a global access level of read-only can be given additional capabilities at the Message VPN level by assigning them a default Message VPN access level or a Message VPN access level exception of read-write. |
|
mesh-manager |
In addition to the capabilities offered by a global access level of read-only, a CLI user with an access level of mesh-manager can:
CLI users with a global access level of mesh-manager can be given additional capabilities at the Message VPN level by assigning them a default Message VPN access level or a Message VPN access level exception of read-write. |
|
read-write |
In addition to the capabilities offered by a global access level of mesh‑manager, a CLI user with an access level of read-write can perform most configuration changes, including:
|
|
admin |
The CLI user has full access to all global and Message VPN-scoped CLI commands (it provides an effective Message VPN access level of read-write). Some configuration changes or actions that can only be performed with a global access level of admin include:
|
VPN Access Levels
The following table provides information on the possible Message VPN access levels that can be assigned to a Solace Event Broker CLI user and many of the capabilities and limitations that those access levels present.
| Level | Capabilities and Limitations... |
|---|---|
|
none (The default value for the default Message VPN access level.) |
The CLI user has no access to Message VPN-scoped CLI commands. |
|
read-only |
The CLI user can:
|
|
read-write |
In addition to the capabilities offered by a Message VPN access level of read-only, a CLI user with a Message VPN access level of read-write can perform most Message VPN scoped configuration changes. Some of configuration changes or actions that are forbidden (and would require a higher global access level of read-write or admin) because they affect system resources include:
Global system administrators are expected to create client profiles that define how clients within a Message VPN are expected to behave. However, a CLI user limited to Message VPN scope does have access to show client profiles and assign client profiles to client username objects. |
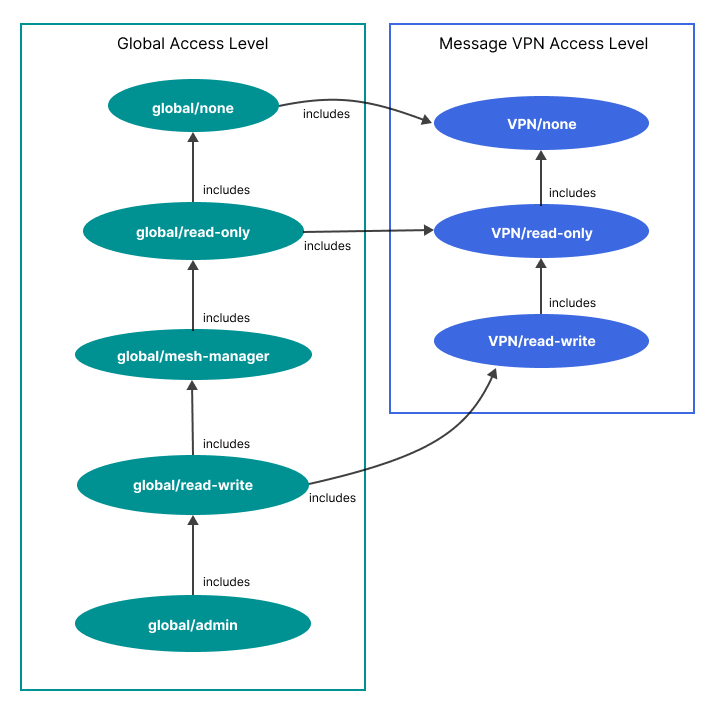
Access Level Relationships
The following diagram summarizes the relationships between each access level. More specifically, it shows how each access level includes the permissions from the previous access level and it also shows the Message VPN access level permissions that are included in each global access level by default.