1 Introduction
Solace Implementation Note
This document provides an annotated version of the full text of the MQTT v5.0 functional specification. MQTT v5.0 is supported by Solace event brokers acting in the role of an MQTT server. The text of the protocol specification is annotated with boxes like this one, which indicate any deviations, limitations, or choices made in the “SHOULD” and “MAY” clauses for the Solace implementation.
Only exceptions to the MQTT v5.0 specification are highlighted – meaning that unless indicated otherwise, the Solace server conforms to each section of the specification.
The target audience for these annotations are application developers developing MQTT clients for use with a Solace MQTT appliance as their MQTT server.
A summary of the functionality supported by Solace is below. Solace software has only a few exceptions from what is required in the MQTT v5.0 specification.
- Server-side role only
- QoS 0 and QoS 1 messages are fully supported. QoS 2 messages from clients are accepted but are treated as QoS 1 messages. QoS 2 subscriptions from clients are accepted but are downgraded to QoS 1. Both of these behaviors are allowed by the specification.
- Will messages are supported with certain limitations.
- Qos 1 shared subscriptions are downgraded to QoS 0.
1.0 Intellectual property rights policy
This specification is provided under the Non-Assertion Mode of the OASIS IPR Policy, the mode chosen when the Technical Committee was established. For information on whether any patents have been disclosed that may be essential to implementing this specification, and any offers of patent licensing terms, please refer to the Intellectual Property Rights section of the TC’s web page (https://www.oasis-open.org/committees/mqtt/ipr.php).
1.1 Organization of the MQTT specification
The specification is split into seven chapters:
- 1 Introduction
- 2 MQTT Control Packet format
- 3 MQTT Control Packets
- 4 Operational behavior
- 5 Security (non-normative)
- 7 Conformance
1.2 Terminology
The key words "MUST", "MUST NOT", "REQUIRED", "SHALL", "SHALL NOT", "SHOULD", "SHOULD NOT", "RECOMMENDED", "MAY", and "OPTIONAL" in this specification are to be interpreted as described in IETF RFC 2119 [RFC2119], except where they appear in text that is marked as non-normative.
A construct provided by the underlying transport protocol that is being used by MQTT.
It connects the Client to the Server.
It provides the means to send an ordered, lossless, stream of bytes in both directions.
Refer to 4.2 Network Connections for non-normative examples.
The data carried by the MQTT protocol across the network for the application. When an Application Message is transported by MQTT it contains payload data, a Quality of Service (QoS), a collection of Properties, and a Topic Name.
A program or device that uses MQTT. A Client:
- opens the Network Connection to the Server
- publishes Application Messages that other Clients might be interested in.
- subscribes to request Application Messages that it is interested in receiving.
- unsubscribes to remove a request for Application Messages.
- closes the Network Connection to the Server.
A program or device that acts as an intermediary between Clients which publish Application Messages and Clients which have made Subscriptions. A Server:
- accepts Network Connections from Clients.
- accepts Application Messages published by Clients.
- processes Subscribe and Unsubscribe requests from Clients.
- forwards Application Messages that match Client Subscriptions.
- closes the Network Connection from the Client.
A stateful interaction between a Client and a Server. Some Sessions last only as long as the Network Connection, others can span multiple consecutive Network Connections between a Client and a Server.
A Subscription comprises a Topic Filter and a maximum QoS. A Subscription is associated with a single Session. A Session can contain more than one Subscription. Each Subscription within a Session has a different Topic Filter.
A Shared Subscription comprises a Topic Filter and a maximum QoS. A Shared Subscription can be associated with more than one Session to allow a wider range of message exchange patterns. An Application Message that matches a Shared Subscription is only sent to the Client associated with one of these Sessions. A Session can subscribe to more than one Shared Subscription and can contain both Shared Subscriptions and Subscriptions which are not shared.
A Wildcard Subscription is a Subscription with a Topic Filter containing one or more wildcard characters. This allows the subscription to match more than one Topic Name. Refer to section 4.7 for a description of wildcard characters in a Topic Filter.
The label attached to an Application Message which is matched against the Subscriptions known to the Server.
An expression contained in a Subscription to indicate an interest in one or more topics. A Topic Filter can include wildcard characters.
A packet of information that is sent across the Network Connection. The MQTT specification defines fifteen different types of MQTT Control Packet, for example the PUBLISH packet is used to convey Application Messages.
A control packet that cannot be parsed according to this specification. Refer to section 4.13 for information about error handling.
An error that is detected after the packet has been parsed and found to contain data that is not allowed by the protocol or is inconsistent with the state of the Client or Server. Refer to section 4.13 for information about error handling.
An Application Message which is published by the Server after the Network Connection is closed in cases where the Network Connection is not closed normally. Refer to section 3.1.2.5 for information about Will Messages.
Disallowed Unicode code point:
The set of Unicode Control Codes and Unicode Noncharacters which should not be included in a UTF-8 Encoded String. Refer to section 1.5.4 for more information about the Disallowed Unicode code points.
1.3 Normative references
Bradner, S., "Key words for use in RFCs to Indicate Requirement Levels", BCP 14, RFC 2119, DOI 10.17487/RFC2119, March 1997,
http://www.rfc-editor.org/info/rfc2119
Yergeau, F., "UTF-8, a transformation format of ISO 10646", STD 63, RFC 3629, DOI 10.17487/RFC3629, November 2003,
http://www.rfc-editor.org/info/rfc3629
Fette, I. and A. Melnikov, "The WebSocket Protocol", RFC 6455, DOI 10.17487/RFC6455, December 2011,
http://www.rfc-editor.org/info/rfc6455
The Unicode Consortium. The Unicode Standard,
http://www.unicode.org/versions/latest/
1.4 Non-normative references
Postel, J., "Transmission Control Protocol", STD 7, RFC 793, DOI 10.17487/RFC0793, September 1981, http://www.rfc-editor.org/info/rfc793
Dierks, T. and E. Rescorla, "The Transport Layer Security (TLS) Protocol Version 1.2", RFC 5246, DOI 10.17487/RFC5246, August 2008,
http://www.rfc-editor.org/info/rfc5246
Advanced Encryption Standard (AES) (FIPS PUB 197).
https://csrc.nist.gov/csrc/media/publications/fips/197/final/documents/fips-197.pdf
ChaCha20 and Poly1305 for IETF Protocols
https://tools.ietf.org/html/rfc7539
Security Requirements for Cryptographic Modules (FIPS PUB 140-2)
https://csrc.nist.gov/csrc/media/publications/fips/140/2/final/documents/fips1402.pdf
IEEE Standard for Local and metropolitan area networks - Secure Device Identity
http://standards.ieee.org/findstds/standard/802.1AR-2009.html
ISO/IEC 29192-1:2012 Information technology -- Security techniques -- Lightweight cryptography -- Part 1: General
https://www.iso.org/standard/56425.html
MQTT supplemental publication, MQTT and the NIST Framework for Improving Critical Infrastructure Cybersecurity
http://docs.oasis-open.org/mqtt/mqtt-nist-cybersecurity/v1.0/mqtt-nist-cybersecurity-v1.0.html
MQTT V3.1.1 Protocol Specification
http://docs.oasis-open.org/mqtt/mqtt/v3.1.1/os/mqtt-v3.1.1-os.html
MQTT V3.1.1 ISO Standard (ISO/IEC 20922:2016)
https://www.iso.org/standard/69466.html
Improving Critical Infrastructure Cybersecurity Executive Order 13636
https://www.nist.gov/sites/default/files/documents/itl/preliminary-cybersecurity-framework.pdf
NISTIR 7628 Guidelines for Smart Grid Cyber Security Catalogue
https://www.nist.gov/sites/default/files/documents/smartgrid/nistir-7628_total.pdf
NSA Suite B Cryptography
http://www.nsa.gov/ia/programs/suiteb_cryptography/
PCI-DSS Payment Card Industry Data Security Standard
https://www.pcisecuritystandards.org/pci_security/
Leech, M., Ganis, M., Lee, Y., Kuris, R., Koblas, D., and L. Jones, "SOCKS Protocol Version 5", RFC 1928, DOI 10.17487/RFC1928, March 1996,
http://www.rfc-editor.org/info/rfc1928
Sermersheim, J., Ed., "Lightweight Directory Access Protocol (LDAP): The Protocol", RFC 4511, DOI 10.17487/RFC4511, June 2006,
http://www.rfc-editor.org/info/rfc4511
Cooper, D., Santesson, S., Farrell, S., Boeyen, S., Housley, R., and W. Polk, "Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile", RFC 5280, DOI 10.17487/RFC5280, May 2008,
http://www.rfc-editor.org/info/rfc5280
Eastlake 3rd, D., "Transport Layer Security (TLS) Extensions: Extension Definitions", RFC 6066, DOI 10.17487/RFC6066, January 2011,
http://www.rfc-editor.org/info/rfc6066
Hardt, D., Ed., "The OAuth 2.0 Authorization Framework", RFC 6749, DOI 10.17487/RFC6749, October 2012,
http://www.rfc-editor.org/info/rfc6749
Santesson, S., Myers, M., Ankney, R., Malpani, A., Galperin, S., and C. Adams, "X.509 Internet Public Key Infrastructure Online Certificate Status Protocol - OCSP", RFC 6960, DOI 10.17487/RFC6960, June 2013,
http://www.rfc-editor.org/info/rfc6960
Sarbanes-Oxley Act of 2002.
http://www.gpo.gov/fdsys/pkg/PLAW-107publ204/html/PLAW-107publ204.htm
U.S.-EU Privacy Shield Framework
Berners-Lee, T., Fielding, R., and L. Masinter, "Uniform Resource Identifier (URI): Generic Syntax", STD 66, RFC 3986, DOI 10.17487/RFC3986, January 2005,
http://www.rfc-editor.org/info/rfc3986
Mockapetris, P., "Domain names - implementation and specification", STD 13, RFC 1035, DOI 10.17487/RFC1035, November 1987,
http://www.rfc-editor.org/info/rfc1035
Gulbrandsen, A., Vixie, P., and L. Esibov, "A DNS RR for specifying the location of services (DNS SRV)", RFC 2782, DOI 10.17487/RFC2782, February 2000,
http://www.rfc-editor.org/info/rfc2782
1.5 Data representation
1.5.1 Bits
Bits in a byte are labelled 7 to 0. Bit number 7 is the most significant bit, the least significant bit is assigned bit number 0.
1.5.2 Two Byte Integer
Two Byte Integer data values are 16-bit unsigned integers in big-endian order: the high order byte precedes the lower order byte. This means that a 16-bit word is presented on the network as Most Significant Byte (MSB), followed by Least Significant Byte (LSB).
1.5.3 Four Byte Integer
Four Byte Integer data values are 32-bit unsigned integers in big-endian order: the high order byte precedes the successively lower order bytes. This means that a 32-bit word is presented on the network as Most Significant Byte (MSB), followed by the next most Significant Byte (MSB), followed by the next most Significant Byte (MSB), followed by Least Significant Byte (LSB).
1.5.4 UTF-8 Encoded String
Text fields within the MQTT Control Packets described later are encoded as UTF-8 strings. UTF-8 [RFC3629] is an efficient encoding of Unicode [Unicode] characters that optimizes the encoding of ASCII characters in support of text-based communications.
Each of these strings is prefixed with a Two Byte Integer length field that gives the number of bytes in a UTF-8 encoded string itself, as illustrated in Figure 1.1 Structure of UTF-8 Encoded Strings below. Consequently, the maximum size of a UTF-8 Encoded String is 65,535 bytes.
Unless stated otherwise all UTF-8 encoded strings can have any length in the range 0 to 65,535 bytes.
Figure 1‑1 Structure of UTF-8 Encoded Strings
|
Bit |
7 |
6 |
5 |
4 |
3 |
2 |
1 |
0 |
|
byte 1 |
String length MSB |
|||||||
|
byte 2 |
String length LSB |
|||||||
|
byte 3 …. |
UTF-8 encoded character data, if length > 0. |
|||||||
The character data in a UTF-8 Encoded String MUST be well-formed UTF-8 as defined by the Unicode specification [Unicode] and restated in RFC 3629 [RFC3629]. In particular, the character data MUST NOT include encodings of code points between U+D800 and U+DFFF[MQTT-1.5.4-1].If the Client or Server receives an MQTT Control Packet containing ill-formed UTF-8 it is a Malformed Packet. Refer to section 4.13 for information about handling errors.
A UTF-8 Encoded String MUST NOT include an encoding of the null character U+0000. [MQTT-1.5.4-2]. If a receiver (Server or Client) receives an MQTT Control Packet containing U+0000 it is a Malformed Packet. Refer to section 4.13 for information about handling errors.
The data SHOULD NOT include encodings of the Unicode [Unicode] code points listed below. If a receiver (Server or Client) receives an MQTT Control Packet containing any of them it MAY treat it as a Malformed Packet. These are the Disallowed Unicode code points. Refer to section 5.4.9 for more information about handling Disallowed Unicode code points.
- U+0001..U+001F control characters
- U+007F..U+009F control characters
- Code points defined in the Unicode specification [Unicode] to be non-characters (for example U+0FFFF)
A UTF-8 encoded sequence 0xEF 0xBB 0xBF is always interpreted as U+FEFF ("ZERO WIDTH NO-BREAK SPACE") wherever it appears in a string and MUST NOT be skipped over or stripped off by a packet receiver[MQTT-1.5.4-3].
Non-normative example
For example,
the string A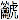 which is LATIN
CAPITAL Letter A followed by the code point U+2A6D4 (which represents a CJK
IDEOGRAPH EXTENSION B character) is encoded as follows:
which is LATIN
CAPITAL Letter A followed by the code point U+2A6D4 (which represents a CJK
IDEOGRAPH EXTENSION B character) is encoded as follows:
Figure 1‑2 UTF-8 Encoded String non-normative example
|
Bit |
7 |
6 |
5 |
4 |
3 |
2 |
1 |
0 |
|
byte 1 |
String Length MSB (0x00) |
|||||||
|
|
0 |
0 |
0 |
0 |
0 |
0 |
0 |
0 |
|
byte 2 |
String Length LSB (0x05) |
|||||||
|
|
0 |
0 |
0 |
0 |
0 |
1 |
0 |
1 |
|
byte 3 |
‘A’ (0x41) |
|||||||
|
|
0 |
1 |
0 |
0 |
0 |
0 |
0 |
1 |
|
byte 4 |
(0xF0) |
|||||||
|
|
1 |
1 |
1 |
1 |
0 |
0 |
0 |
0 |
|
byte 5 |
(0xAA) |
|||||||
|
|
1 |
0 |
1 |
0 |
1 |
0 |
1 |
0 |
|
byte 6 |
(0x9B) |
|||||||
|
|
1 |
0 |
0 |
1 |
1 |
0 |
1 |
1 |
|
byte 7 |
(0x94) |
|||||||
|
|
1 |
0 |
0 |
1 |
0 |
1 |
0 |
0 |
1.5.5 Variable Byte Integer
The Variable Byte Integer is encoded using an encoding scheme which uses a single byte for values up to 127. Larger values are handled as follows. The least significant seven bits of each byte encode the data, and the most significant bit is used to indicate whether there are bytes following in the representation. Thus, each byte encodes 128 values and a "continuation bit". The maximum number of bytes in the Variable Byte Integer field is four. The encoded value MUST use the minimum number of bytes necessary to represent the value[MQTT-1.5.5-1]. This is shown in Table 1‑1 Size of Variable Byte Integer.
Table 1‑1 Size of Variable Byte Integer
|
Digits |
From |
To |
|
1 |
0 (0x00) |
127 (0x7F) |
|
2 |
128 (0x80, 0x01) |
16,383 (0xFF, 0x7F) |
|
3 |
16,384 (0x80, 0x80, 0x01) |
2,097,151 (0xFF, 0xFF, 0x7F) |
|
4 |
2,097,152 (0x80, 0x80, 0x80, 0x01) |
268,435,455 (0xFF, 0xFF, 0xFF, 0x7F) |
Non-normative comment
The algorithm for encoding a non-negative integer (X) into the Variable Byte Integer encoding scheme is as follows:
do
encodedByte = X MOD 128
X = X DIV 128
// if there are more data to encode, set the top bit of this byte
if (X > 0)
encodedByte = encodedByte OR 128
endif
'output' encodedByte
while (X > 0)
Where MOD is the modulo operator (% in C), DIV is integer division (/ in C), and OR is bit-wise or (| in C).
Non-normative comment
The algorithm for decoding a Variable Byte Integer type is as follows:
multiplier = 1
value = 0
do
encodedByte = 'next byte from stream'
value += (encodedByte AND 127) * multiplier
if (multiplier > 128*128*128)
throw Error(Malformed Variable Byte Integer)
multiplier *= 128
while ((encodedByte AND 128) != 0)
where AND is the bit-wise and operator (& in C).
When this algorithm terminates, value contains the Variable
Byte Integer value.
1.5.6 Binary Data
Binary Data is represented by a Two Byte Integer length which indicates the number of data bytes, followed by that number of bytes. Thus, the length of Binary Data is limited to the range of 0 to 65,535 Bytes.
1.5.7 UTF-8 String Pair
A UTF-8 String Pair consists of two UTF-8 Encoded Strings. This data type is used to hold name-value pairs. The first string serves as the name, and the second string contains the value.
Both strings MUST comply with the requirements for UTF-8 Encoded Strings[MQTT-1.5.7-1]. If a receiver (Client or Server) receives a string pair which does not meet these requirements it is a Malformed Packet. Refer to section 4.13 for information about handling errors.
1.6 Security
MQTT Client and Server implementations SHOULD offer Authentication, Authorization and secure communication options, such as those discussed in Chapter 5. Applications concerned with critical infrastructure, personally identifiable information, or other personal or sensitive information are strongly advised to use these security capabilities.
1.7 Editing convention
Text highlighted in Yellow within this specification identifies conformance statements. Each conformance statement has been assigned a reference in the format [MQTT-x.x.x-y] where x.x.x is the section number and y is a statement counter within the section.
1.8 Change history
1.8.1 MQTT v3.1.1
MQTT v3.1.1 was the first OASIS standard version of MQTT [MQTTV311].
MQTT v3.1.1 is also standardized as ISO/IEC 20922:2016 [ISO20922].
1.8.2 MQTT v5.0
MQTT v5.0 adds a significant number of new features to MQTT while keeping much of the core in place. The major functional objectives are:
- Enhancements for scalability and large scale systems
- Improved error reporting
- Formalize common patterns including capability discovery and request response
- Extensibility mechanisms including user properties
- Performance improvements and support for small clients
Refer to Appendix C for a summary of changes in MQTT v5.0.