Networking Options for Dedicated Cluster Deployments
In Dedicated Clusters, we deploy the Mission Control Agent and event broker services in a region controlled by Solace. If you require private Messaging Connectivity between the event broker services in your Dedicated Cluster and the virtual private cloud (VPC) where your client applications reside, we offer several networking options supported by your chosen cloud provider.
When deciding on the networking options for your Messaging Connectivity, consider the requirements of your entire estate, including:
-
whether you need bidirectional or unidirectional network connectivity
-
the amount of event broker services you want, or may require in the future
-
bandwidth limitations
-
support for multiple regions
-
support for transitive routing
The tables below show the networking options supported by each of the cloud providers available for Dedicated Clusters. They also provide information about the benefits and limitations of each option and links to any related documentation. Each table provides information about a specific cloud provider:
You can see an overview of each networking option, including architectural diagrams, in Overview of Supported Networking Options for Dedicated Clusters.
See Supported Networking Options for Dedicated Clusters by Cloud Providers Supported by Solace for tables showing the Messaging Connectivity options supported by Solace for each cloud provider.
Overview of Supported Networking Options for Dedicated Clusters
The sections below provide an overview and diagram of each of the networking options supported by Solace for Messaging Connectivity for Dedicated Clusters.
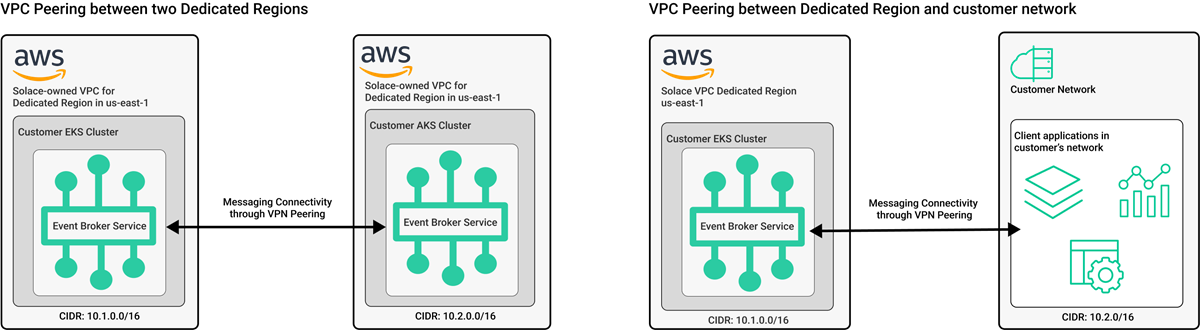
Virtual Private Cloud (VPC) and Virtual Network (VNet) Peering
With virtual private cloud (VPC) or virtual network (VNet) peering, Solace connects your Dedicated Cluster with another Dedicated Cluster in the same cloud provider, or with your network. Multiple Dedicated Clusters and networks can be connected together this way.
The diagram below provides examples of VPC/VNet peering between two Dedicated Clusters and VPC/VNet peering between a Dedicated Cluster and a customer network.
VPC/VNet peering is available for every cloud provider Solace deploys Dedicated Clusters to:
- Benefits
- VPC/VNet peering is the simplest network solution for Messaging Connectivity.
- Security Considerations
-
Traffic can flow in both directions between the peered Dedicated Cluster and your network if your routing rules allow it. This can be useful if you want to enable certain features, like REST Delivery Points (RDP) for your event broker services, which require both outbound and inbound connections.
- Drawbacks
-
The CIDR ranges of your Dedicated Clusters and networks must be unique. They cannot overlap or match.
-
Transitive peering is only available for Dedicated Clusters deployed to Azure Kubernetes Service (AKS).
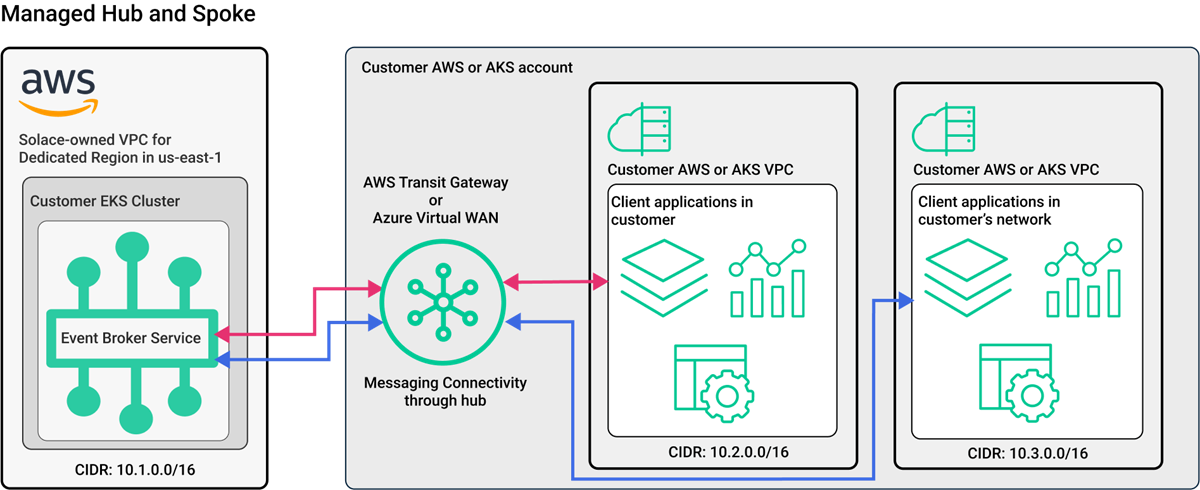
Managed Hub-and-Spoke Networking
With managed hub-and-spoke networking, Solace connects your Dedicated Cluster to your network transit hub, which connects to other Dedicated Clusters, or your virtual private clouds and networks.
The diagram below provides an example of managed hub-and-spoke networking between a Dedicated Cluster and customer networks through a customer-owned hub.
The following managed hub-and-spoke networking options are supported by Solace:
- Benefits
-
Connectivity between the networks hosting your event broker services are simplified. You only have to worry about a single connection for each datacenter.
- Security Considerations
-
Traffic can flow in both directions between the peered Dedicated Cluster and your network if your routing rules allow it. This can be useful if you want to enable certain features, like RDPs for your event broker services, which require both outbound and inbound connections.
- Drawbacks
-
Solace recommends using unique CIDR ranges for your Dedicated Cluster and your networks when using managed hub-and-spoke for Messaging Connectivity.
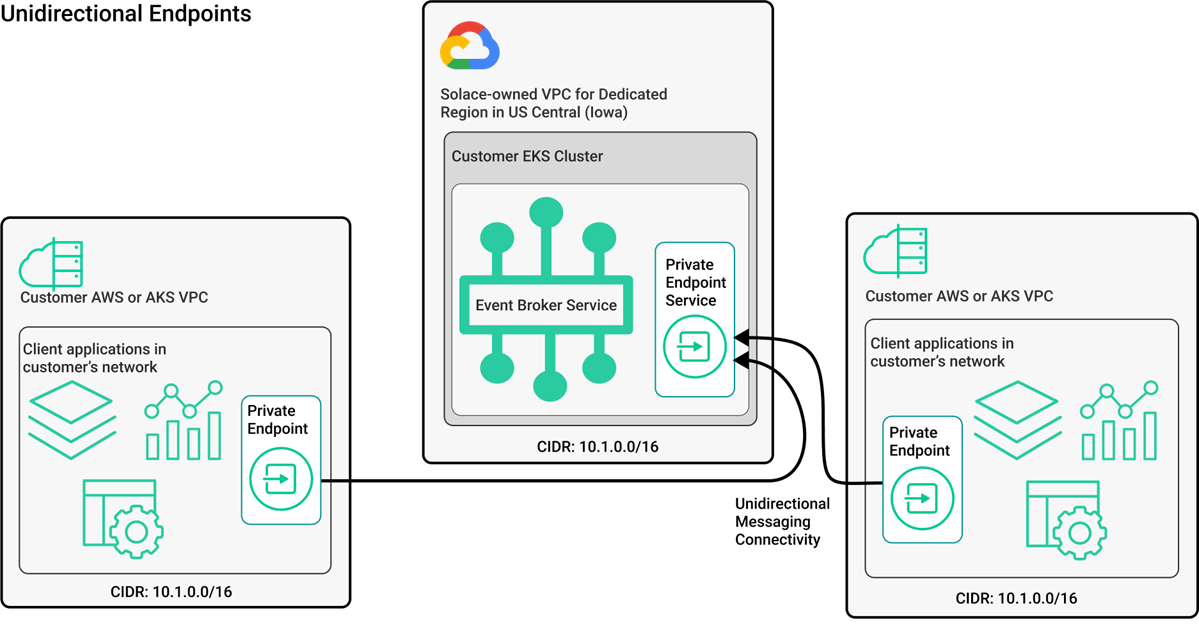
Unidirectional Endpoints
With unidirectional endpoints, Solace connects the Dedicated Cluster to your network by exposing an event broker service endpoint in your network. Traffic flows through the private endpoint, to and from the event broker service.
The following diagram provides an example of unidirectional endpoints, with private endpoints connecting customer networks to the event broker service in your Dedicated Cluster.
The following unidirectional endpoints options are available for connecting your Dedicated Cluster to your networks:
- Benefits
-
It doesn't matter if the CIDR range of your network and your Dedicated Cluster match, or overlap.
-
Network peering between the Dedicated Cluster and your network is not possible.
- Drawbacks
-
Communication is unidirectional. This means that features like RDP and Kafka Bridge won't work unless the destinations are accessible via the public internet.
-
Setup is done with event broker service creation instead of when the Dedicated Cluster is created, which complicates manual configuration.
-
Source IP addresses cannot be preserved, so event broker ACLs can't filter on source and debugging client connections can be complicated
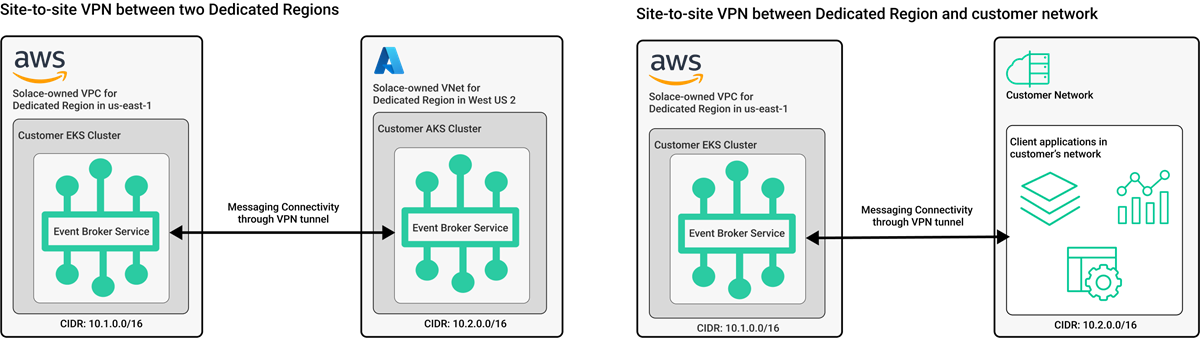
Site-to-Site Virtual Private Network (VPN)
With site-to-site virtual private networking (VPN), Solace connects the Dedicated Cluster with another Dedicated Cluster, or with your network. Multiple Dedicated Clusters and networks can be connected together this way.
Using site-to-site VPN for the Messaging Connectivity for your Dedicated Cluster is an additional add-on purchase. Contact Solace for information.
This diagram below provides examples of site-to-site VPN network between two Dedicated Clusters deployed to different cloud providers, and site-to-site VPN between a Dedicated Cluster and a customer network.
Site-to-site VPN is available for every cloud provider Solace deploys Dedicated Clusters to:
If you choose to use site-to-site VPN, you must complete the site-to-site VPN questionnaire for Dedicated Cluster deployments. For more information, see Questionnaire: Site-to-Site VPN for Dedicated Cluster Deployments .
- Benefits
- Site-to-site VPN is the only option if your VPC or network is partially or completely on-premises, or if you want to connect multiple Dedicated Clusters in different cloud providers (multi-cloud).
- Drawbacks
- Site-to-site VPN is an add-on purchase, and is not included by default for Dedicated Cluster deployments.
Supported Networking Options for Dedicated Clusters by Cloud Providers Supported by Solace
The tables below show the networking options supported by each of the cloud providers available for Dedicated Clusters. They also provide information about the benefits and limitations of each option and links to any related documentation. Each table provides information about a specific cloud provider:
-
Supported Networking Options for Dedicated Clusters in Azure Kubernetes Service (AKS)
-
Supported Networking Options for Dedicated Clusters in Amazon Elastic Kubernetes Service (EKS)
-
Supported Networking Options for Dedicated Clusters in Google Kubernetes Engine (GKE)
Supported Networking Options for Dedicated Clusters in Azure Kubernetes Service (AKS)
You can configure the Messaging Connectivity for your Dedicated Cluster deployment in an AKS cluster with the following networking options:
| Azure Kubernetes Service (AKS) | ||||||
|---|---|---|---|---|---|---|
| Networking Option | Description | Benefits and Drawbacks |
Bandwidth Limits |
Multi-Region | Transitive Routing |
Further reading |
| Azure VNET Peering |
Allows Messaging Connectivity between different VPCs Messaging Connectivity can include:
|
Benefits:
Limitations:
|
None | Yes | Yes | Azure Virtual network peering documentation |
| Azure Virtual WAN |
Azure's version of managed hub-and spoke network connectivity. The Dedicated Cluster attaches to your Azure Virtual WAN, which performs all routing, and can optionally include a firewall. Azure Virtual WAN can also do perform other network activities, such as VPN, ExpressRoute/Direct Connect, etc. |
Benefits:
Limitations:
|
Up to 50 Gbps for VNET-to-VNET traffic Up to 20 Gbps for VPN and virtual hub traffic |
Attachments must be in the same region. You can connect Azure Virtual WAN hubs together to connect regions. |
Yes | Azure Virtual WAN documentation |
| Azure Private Link |
Azure's version of uni-directional endpoints. Private Link uses a private endpoint to expose an endpoint of your event broker service directly to your network. Messaging traffic travels through the endpoint, over the Microsoft backbone network and is not exposed to the public internet. |
Benefits:
Limitations:
|
None | Yes | Not applicable | Azure Private Link documentation |
| Site-to-site VPN |
Solace uses a VPN to connect your Dedicated Cluster to one, or many of your networks. The networks can be on premises, in the cloud, or a combination. or Solace uses a VPN to connect many of your Dedicated Clusters together (multi-cloud). |
Benefits:
Limitations:
|
Depends on the selected solution:
|
Yes | Contact Solace for information. | |
Supported Networking Options for Dedicated Clusters in Amazon Elastic Kubernetes Service (EKS)
You can configure the Messaging Connectivity for your Dedicated Cluster deployment in an EKS cluster with the following networking options:
| Amazon Elastic Kubernetes (EKS) | ||||||
|---|---|---|---|---|---|---|
| Networking Option | Description | Benefits and Limitattions | Bandwidth Limits |
Multi-Region | Transitive Routing |
Further reading |
| VPC Peering |
Allows Messaging Connectivity between different VPCs. Messaging Connectivity can include:
|
Benefits:
Limitations:
|
None | Yes | Yes | AWS VPC Peering documentation |
| AWS Transit Gateway |
Amazon's version of managed hub-and spoke network connectivity. The Dedicated Cluster attaches to your AWS Transit Gateway, which performs all routing, and can optionally include a firewall. AWS Transit Gateway can also perform other network activities, such as VPN, ExpressRoute, Direct Connect, etc. |
Benefits:
Limitations:
|
Up to 100 Gbps per Availability Zone per attachment. |
Attachments must be in the same region. You can connect AWS Transit Gateway together to connect regions. |
Yes, but must be through the Transit Gateway | |
| Site-to-site VPN |
Solace uses a VPN to connect your Dedicated Cluster to one, or many of your networks. The networks can be on premises, in the cloud, or a combination. or Solace uses a VPN to connect many of your Dedicated Clusters together (multi-cloud). |
Benefits:
Limitations:
|
1.25 Gbps per VPN tunnel (two tunnels are required per connection) | Yes | Contact Solace for information. | |
Supported Networking Options for Dedicated Clusters in Google Kubernetes Engine (GKE)
You can configure the Messaging Connectivity for your Dedicated Cluster deployment in an GKE cluster with the following networking options:
| Google Kubernetes Engine (GKE) | ||||||
|---|---|---|---|---|---|---|
| Networking Option | Description | Benefits and Limitattions | Bandwidth Limits |
Multi-Region | Transitive Routing |
Further reading |
| VPC Peering |
Allows Messaging Connectivity between different VPCs . Messaging Connectivity can include:
|
Benefits:
Limitations:
|
None | Yes | No | GCP VPC Peering documentation |
| Private Service Connect |
Google's version of uni-directional endpoints. Private Service Connect uses a private endpoint to expose an endpoint of the event broker service directly to your network. Messaging traffic travels through the endpoint, over the Google Cloud, and is not exposed to the public internet.
|
Benefits:
Limitations:
|
None | Yes | Not applicable | GCP Private Service Connect documentation |
| Site-to-site VPN |
Solace uses a VPN to connect your Dedicated Cluster to one, or many of your networks. The networks can be on premises, in the cloud, or a combination. or Solace uses a VPN to connect many of your Dedicated Clusters together (multi-cloud). |
Benefits:
Limitations:
|
250,000 packets per second. Equivalent to approximately 1-3 Gbps, depending on packet size. | Yes | Contact Solace for information. | |