Solace Cloud Connectivity Requirements
The connectivity model refers to the network access and permissions that allow your Kubernetes cluster and event broker services to function correctly. The types of connectivity you need to consider in your deployment are:
- Messaging Connectivity: The connectivity required for messaging traffic (between event broker services and from applications and external systems to event broker services).
- Management Connectivity: The connectivity required for you to administer your event broker services using the Solace Event Broker CLI, Broker Manager, or SEMP.
- Operational Connectivity: The connectivity required to set up your Kubernetes cluster and launch event broker services.
For more information, see:
Messaging Connectivity
Messaging Connectivity refers to the way messaging clients access the event broker services. A messaging client can connect in three ways: via the public internet, via private IP addresses, or via a hybrid of both.
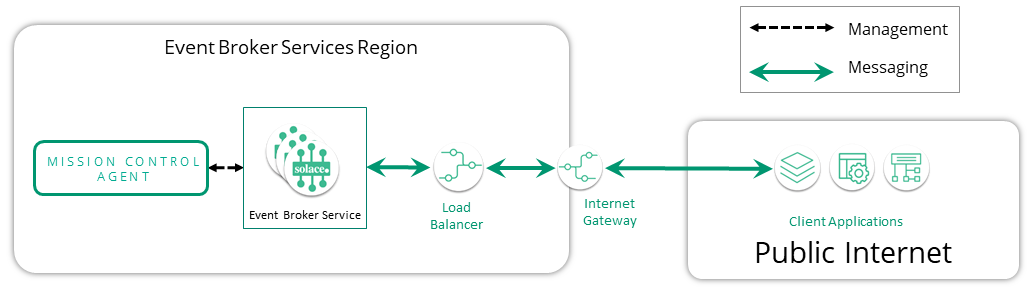
- Public Internet: Messaging clients connect to the event broker service endpoints over the public internet.
- Private IP Addresses: Messaging clients connect to the event broker service endpoints via private routes inside the customer's network.
- Hybrid: Messaging clients in internal networks and in the customer's cloud networks connect via network peering.
Your Messaging Connectivity requirements may influence the ownership model you choose. For Dedicated Clusters, Solace has a list of defined networking options for Messaging Connectivity. These networking options are based on the cloud provider you choose for your Dedicated Cluster. You can review the networking options available for each cloud provider, as well as their benefits and limitations, in Networking Options for Dedicated Cluster Deployments.
If you require a different form of networking for your Messaging Connectivity, you can choose to deploy to a Customer-Controlled Cluster where you have control over network configuration. For a summary of how you can combine different deployment options, see Deployment Options Comparison.
For details about Messaging Connectivity and its use cases, see Management Connectivity for Event Broker Services and Messaging Connectivity for Outbound Connections and Client Applications.
For examples of how each type of Messaging Connectivity works, including diagrams, see:
Public Internet
As shown in the simplified diagram below, this model makes use of an internet gateway and a load balancer to provide access to event broker services for messaging applications that reside in the public internet.
Private IP Addresses
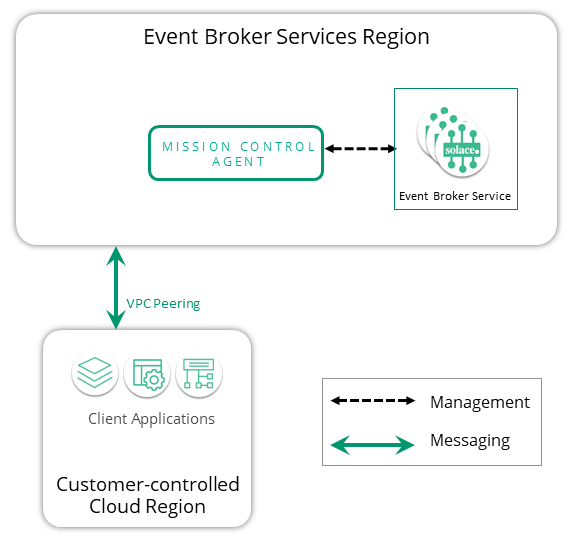
Private IP addresses connect messaging applications to event broker services over private routes inside your (customer) network. Depending on where the applications reside, it may be necessary to enable network peering between the client application VPC/VNet and the VPC/VNet where the event broker service resides. Network peering is an interconnection of administratively separate networks to allow them to exchange traffic.
The following diagram illustrates how client applications in private VPCs/VNets can connect to event broker services in another VPC/VNet.
Hybrid Connectivity
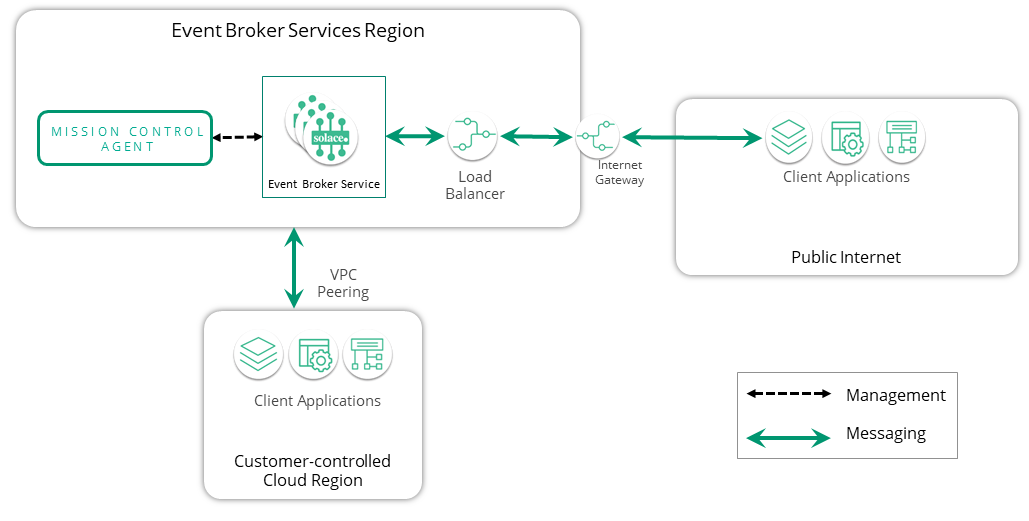
With a hybrid connectivity model, the network is configured to allow access to event broker services for both client applications in internal customer-controlled VPCs/VNets and client applications connecting over the public Internet.
The diagram below shows a simplified illustration of this connectivity option:
Management Connectivity
Management Connectivity is required so that you can administer your event broker services. This category includes connectivity:
- over SSH to the Solace Event Broker CLI
- from a browser to Broker Manager
- from applications to the event broker services using SEMP (requires the correct ports enabled)
For details about Messaging Connectivity, see Management Connectivity for Event Broker Services.
Operational Connectivity
Operational Connectivity refers to the network access you need to set up your Kubernetes cluster and launch event broker services. This includes connectivity from:
- the Kubernetes cluster to the Solace Container Registry (this is optional; you can use a mirror repository instead)
- the Insights Agent to Datadog Home
- the Mission Control Agent to everything (Home Cloud, event broker services, Kubernetes cluster, Amazon S3)
For details about operational connectivity, see Operational Connectivity.