Security Architecture for Solace Cloud
Solace Cloud is highly available and secure
In Solace Cloud, architecture is partially determined by the deployment options you choose, which specifies where your event brokers reside. These deployment-based architecture differences affect various aspects of security and can determine whether you (the customer) or Solace is responsible for certain security tasks in your deployment. To understand the security architecture, you should first understand the differences between the deployment options.
Deployment Options
The deployment options can be broken down to the ownership model that the customer chooses and its connectivity.
- Ownership Model
-
The ownership model refers to the location of the region where the Mission Control Agent and software event brokers are installed. These are the variants of ownership:
- Public Clusters: Dedicated event broker services are deployed in Solace-controlled shared VPC/VNets on public cloud providers such as Amazon Web Services (AWS), Google Cloud Platform (GCP), and Azure.
- Dedicated Clusters: Dedicated event broker services are deployed in Solace-controlled VPC/VNets dedicated to the customer on public cloud providers such as AWS, GCP, and Azure.
- Customer-Controlled Clusters: Dedicated event broker services are deployed in a customer's on-premises or cloud-based Kubernetes cluster, such as OpenShift, Rancher (RKE2), Amazon (EKS), Azure (AKS, ARO), Google (GKE), Alibaba (ACK), Huawei (CCE), Oracle Kubernetes Engine (OKE) and more.
- The ownership determines who is responsible for the security of the infrastructure and connectivity and is summarized as follows:
- The infrastructure in Solace-controlled regions (Public Clusters and Dedicated Clusters) is secure by default for the customer because Solace manages the security for the infrastructure. The customer and Solace collaborate to ensure connectivity requirements are satisfied.
- In Customer-Controlled Clusters, the customer must manage the security for the infrastructure as well as the connectivity requirements.
-
- Connectivity
-
The connectivity model refers to the network access and permissions that allow your Kubernetes cluster and event broker services to function correctly. The types of connectivity you need to consider in your deployment are:
- Messaging Connectivity: The connectivity required for messaging traffic (between event broker services and from applications and external systems to event broker services).
- Management Connectivity: The connectivity required for you to administer your event broker services using the Solace Event Broker CLI, Broker Manager, or SEMP.
- Operational Connectivity: The connectivity required to set up your Kubernetes cluster and launch event broker services.
- Additional network configuration for Dedicated Clusters is required for messaging clients to connect to the event broker services and the responsibility is related to the ownership model chosen as follows:
- For deployments in Public Clusters, the customer manages the access of client applications within a private network to the event broker services. The customer is required to set up the connectivity from the private IP addresses or hybrid configurations (e.g., permit external access to the public Internet or configure VPC/VNet peering).
- For deployments in Dedicated Clusters, the customer manages the access of client applications within a private network to the event broker services. Solace and the customer collaborate to ensure that the deployment matches the customer's messaging connectivity requirements. For example, if the customer has client applications that reside in a private network (i.e., private IP addresses within a VPC/VNet), Solace exchanges route information with the customer to set up VPC/VNet peering, AWS Transit Gateway, or set up connectivity in the Dedicated Cluster.
- For deployments in Customer-Controlled Clusters, the customer manages the connectivity and takes care of setting up the necessary configuration for connectivity from their client applications to their event broker services. (e.g., VPC/VNet peering, site-to-site VPN, AWS Direct Connect, Transit Gateway, loadbalancer, NAT configuration, etc.).
-
For more information about deployment options and connectivity, see Solace Cloud Deployment Ownership Models and Solace Cloud Connectivity Requirements.
For more information about the security responsibilities of the customer and Solace based on the deployment model and ownership, see Customer Roles and Responsibilities for Security.
Security Considerations
All Solace Cloud deployments have well-defined architectures that share the same security considerations. The option you choose determines whether Solace or you (the customer) are responsible for managing different aspects of security. The security architecture considerations for Solace Cloud include:
- Do the event broker services need to be publicly available from the Internet?
- For publicly accessible event broker services, they can be deployed to Public Clusters. You can also choose to deploy to a Dedicated Clusters or Customer-Controlled Clusters.
- For non-public event broker services, Solace recommends that deployments be made in a Kubernetes cluster within an isolated virtual private cloud or virtual network (VPC/VNet). These type of deployments are available in Dedicated Clusters or Customer-Controlled Clusters.
- What is the connectivity model used to access event broker services?
- The messaging connectivity model that the customer chooses for client applications may influence the requirements for the Operational Connectivity (that is, the connectivity to the Solace Home Cloud and the central monitoring service). Operational Connectivity to Home Cloud and the central monitoring service is a requirement for event broker services to function and is not optional. You can use either Public Clusters, Dedicated Clusters, or Customer-Controlled Clusters.
- Solace recommends that client applications connect using VPC/VNet peering or loadbalancer when using private IP addresses. It is possible to deploy event broker services in the same Kubernetes cluster alongside the client applications that use the event broker services. This configuration may be a preferred deployment option based on the customer's security requirements. This option is available only in Customer-Controlled Clusters.
Security Architecture Overview
All supported deployment models permit Solace Cloud to meet various security requirements.
In addition to the deployment model, another factor to consider as part of the customer's security planning is how client applications connect. There are two types of client applications:
- publishers and subscriber applications that use event broker services for messaging and passing data; these applications often connect from another VPC/VNet or from public infrastructure
- optionally, the customer can create management applications that manage the lifecycle of an event broker service; these applications are usually account specific
For more information about connectivity, see Client Application Connectivity and Security.
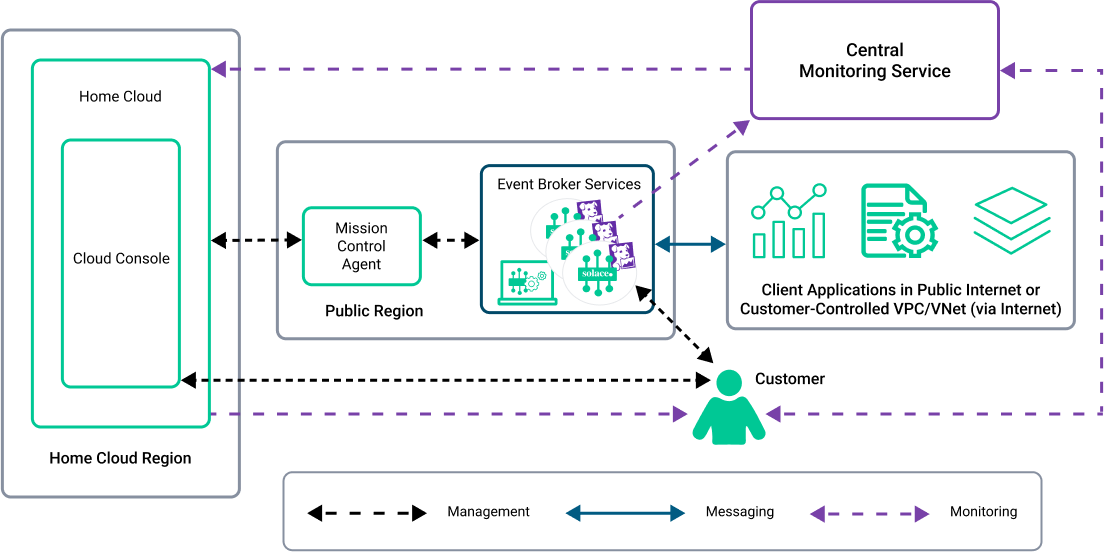
Regardless of the ownership model and connectivity options, each deployment uses a common set of components as shown in the following diagram:
| Component | Description |
|---|---|
|
Home Cloud Region |
Solace has regional site for the Solace Home Cloud. The Home Cloud regions do not share infrastructure, data, or any other system, account, or user information with each other. |
|
Home Cloud |
The Solace Home Cloud is a collection of microservices that provides the control plane for deployments of Solace Cloud. |
|
Cloud Console |
The Solace Cloud Console is a web-based user-interface that gives customers access to Solace Cloud functionality. |
|
Deployment Region |
The region where the Mission Control Agent and software event brokers are installed based on the ownership model. The regions include:
|
|
Mission Control Agent |
The Mission Control Agent is a microservice that is required to deploy and manage event broker services. |
|
Event Management Agent |
The Event Management Agent is an optional component required to discover runtime data and configure event brokers using Event Portal. Depending on your implementation, it may be managed in the datacenter by Solace or installed locally and self-managed. |
|
Event Broker Services |
Event brokers provide the data path to allow applications to communicate in real time. An event broker service in Solace Cloud is either a standalone software event broker or a high-availability group of three software event brokers. |
|
Central Monitoring Service |
The central monitoring service collects monitoring data (statistics/metrics) and logs from event broker services and stores the information. Operational monitoring metrics, statistics, and logs are centrally monitored from the Home Cloud. The central monitoring service is provided by Datadog. Insights Agents are configured for each event broker service to send monitoring data and logs to the central monitoring service. |
|
Client Applications |
A client application can be a program, process, microservice, IoT device, integration component or other runnable consumer, producer, or processor that subscribes to or publishes events through an event broker. Applications may reside on the public Internet or in a customer-controlled region. |
|
Management Data |
Management data is sent between the Mission Control Agent, Home Cloud, and event broker services. Management data includes configuration information for event broker services and metadata that is sent back to Solace through secure ports. |
|
Messaging Data |
Messaging data, which includes payloads of event messages, refers to the information sent between event broker services and the publishing and subscribing client applications. |
|
Monitoring Data |
Monitoring data includes statistics and event broker logs that are sent to the central monitoring service through secure ports. |
For more information about each of the components as they relate to security, see the following sections:
- Solace Home Cloud Security
- Solace Cloud Console Security
- Mission Control Agent Security
- Broker Manager Security
- Event Management Agent
- Event Broker Service Security
- Central Monitoring Service and Insights Agents
- Connection Details for Deployment
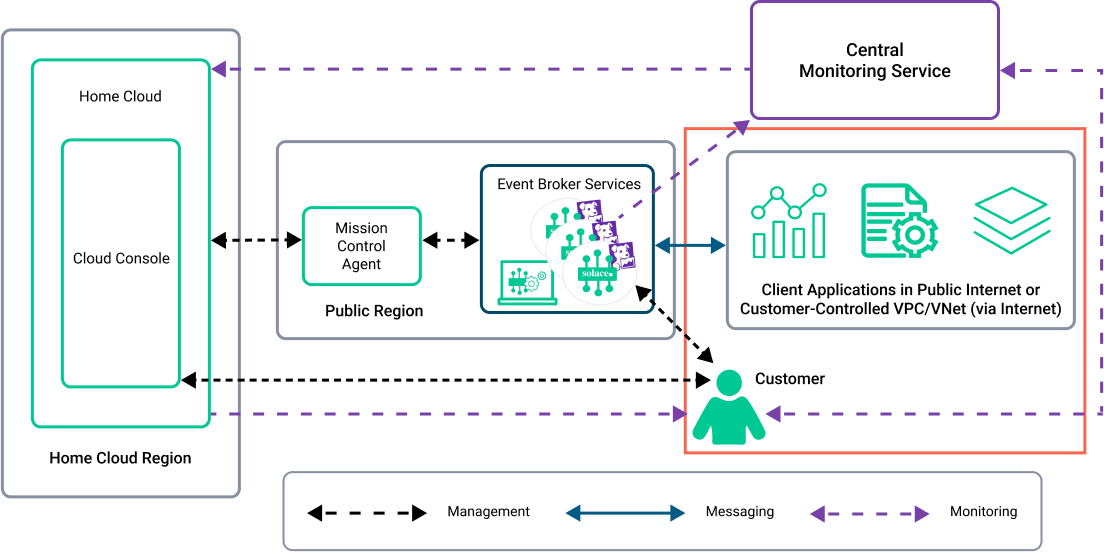
Security Architecture for Public Clusters
In Public Clusters, the event broker services are deployed in a publicly accessible, shared region that is controlled and managed by Solace. Client applications access the event broker services over the public Internet. Solace manages the infrastructure, and always uses the most recent security practices.
The event broker services are deployed to shared Kubernetes clusters per region (Google Cloud Platform) or shared VPCs/VNets per region (AWS or Azure), depending on the cloud provider chosen.
Public Cluster deployments are best suited for environments where client applications access services from the public Internet. These can also include client applications from within a customer network, but in this situation, the customer must manage the access to applications from their own private network to the Internet.
In the following diagram, the red box shows the customer's security architecture responsibilities:
For a summary of the security responsibilities, see Customer Roles and Responsibilities for Security.
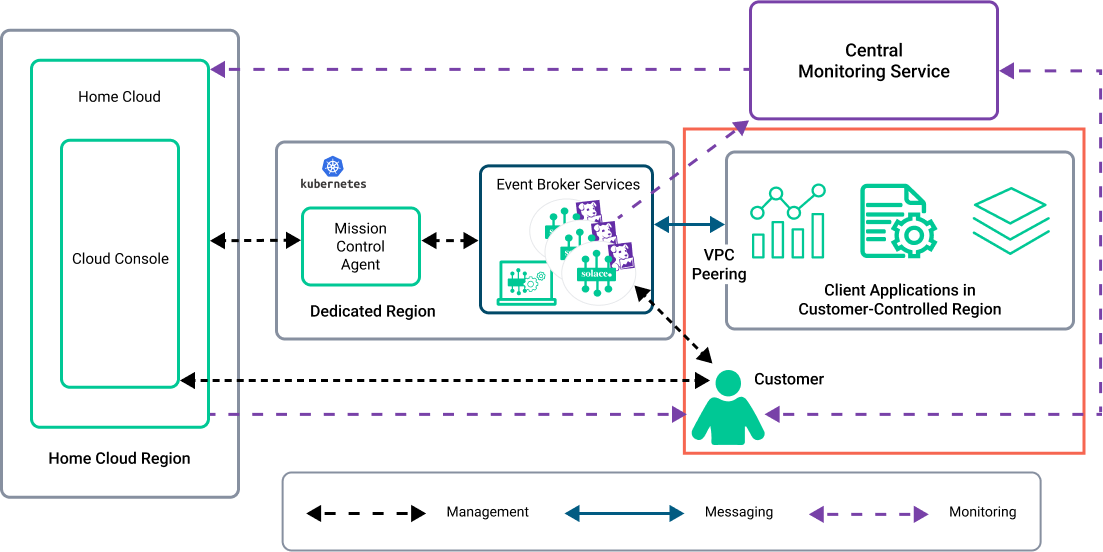
Security Architecture for Dedicated Clusters
In deployments in Dedicated Clusters, Solace also manages the infrastructure using the most recent security practices. Solace ensures that the configuration of the Kubernetes cluster is secure and that your client applications have connectivity.
In this option, the event broker services are run within infrastructure that is dedicated to the customer; usually event broker services are not publicly accessible from the Internet. Client applications access the event broker service from another private network, which is customer-controlled.
This option is ideal when client applications do not access the event broker services from the public Internet. Client applications can connect using VPC/VNet peering technology. It is also possible to configure this option to use a hybrid connectivity model.
In the following diagram, the red box shows the customer's security architecture responsibilities:
For a summary of the security responsibilities, see Customer Roles and Responsibilities for Security.
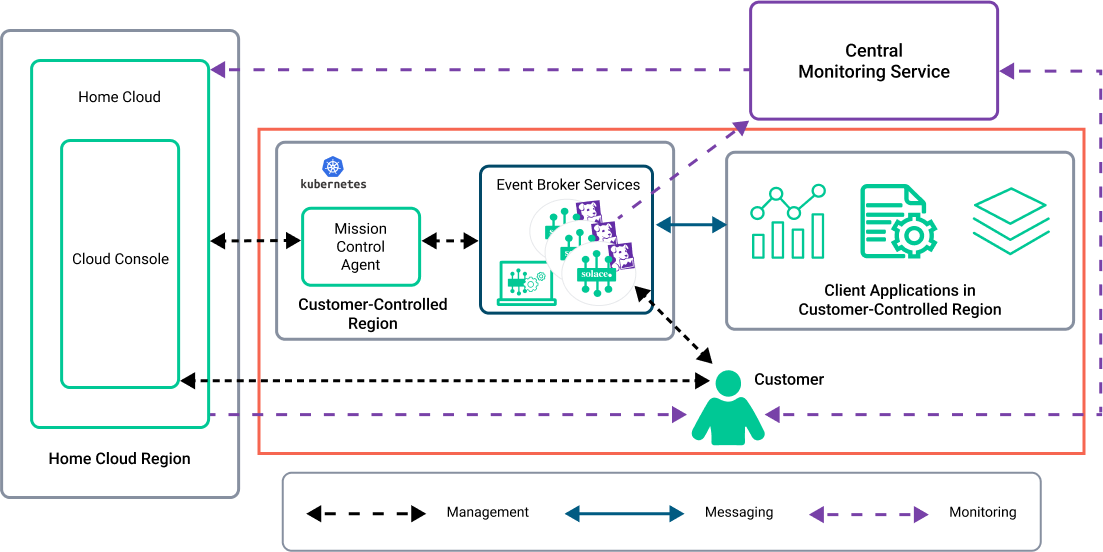
Security Architecture for Customer-Controlled Clusters
In Customer-Controlled Clusters, the customer deploys the event broker services to a dedicated private network, which the customer controls. A Customer-Controlled Cluster gives the customer the most control over security, network configuration, and segregation to deploy event broker services and configure their infrastructure. The customer also controls the Kubernetes cluster (which can be either on-premises or in the cloud) and all aspects of the VPC/VNet where the Kubernetes cluster resides.
In summary, deployments of event broker services on Customer-Controlled Clusters require that the customer considers the following as part of their security planning:
- The requirements for the event broker services, such as whether the deployment requires user accounts that are configured with the required permissions to run and operate correctly. The customer may need to coordinate with their internal infrastructure and security teams to properly set up the user accounts.
- The Mission Control Agent is provided with account permissions to manage event broker services in the customer's Kubernetes cluster. Solace recommends that a very limited set of permissions are assigned account for the Mission Control Agent to limit the risks and the vectors of attack. For more information about the Mission Control Agent, see Mission Control Agent Security.
- Metrics and monitoring data is vital for the Solace Cloud solution to work; it ensures that the event broker services are operating correctly. This system-level data identifies the event broker services so that Solace can properly monitor it as a SaaS. Solace doesn't and cannot access the contents of the messages (data) transported on the customer's network. For Solace Cloud to function correctly, the customer must permit outgoing monitoring traffic from their VPC/VNet.
With deployments in Customer-Controlled Clusters, the customer manages all aspects of the deployment configuration, connectivity, and security. For details, see Kubernetes in Customer-Controlled Clusters .
Kubernetes in Customer-Controlled Clusters
For deployments in Customer-Controlled Clusters, Solace supports the following Kubernetes implementations:
- On-premises:
- Red Hat OpenShift
- Rancher (RKE2)
- VMware Tanzu Kubernetes Grid (TKG)
- In the cloud:
- Alibaba Cloud Container Service for Kubernetes (ACK)
- Amazon Elastic Kubernetes Service (EKS)
- Azure Kubernetes Service (AKS)
- Azure Red Hat OpenShift (ARO)
- Google Kubernetes Engine (GKE)
- Huawei Cloud Container Engine (CCE)
- Oracle Kubernetes Engine (OKE)
In these deployments the customer controls the management of the resources, configuring the networking, and overall security of the Kubernetes cluster. The customer can coordinate with Solace to deploy Solace Cloud.
Prior to working with Solace, the security and permissions in the customer's Kubernetes cluster should be defined and implemented before installing Solace Cloud.
In the following diagram, the red box shows the customer's security architecture responsibilities:
For a summary of the security responsibilities, see Customer Roles and Responsibilities for Security.