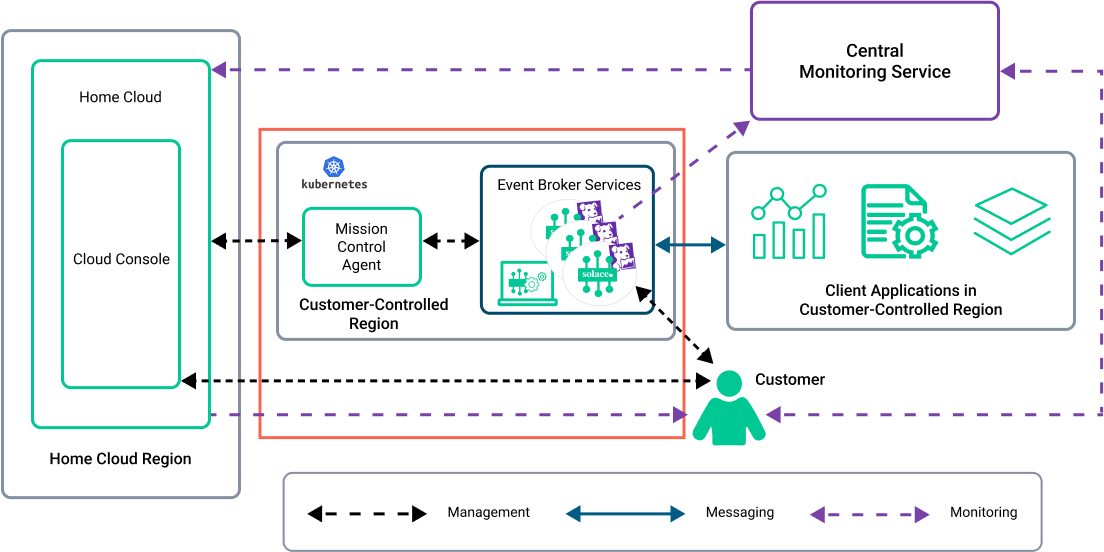
VPC/VNet Isolation
You can deploy your event broker services in a Kubernetes cluster in an isolated virtual private cloud or virtual network (VPC/VNet). An isolated VPC/VNet is recommended when you need additional security and want to keep your event broker services entirely separated from other enterprise applications/services and environments to limit risks and the vectors of attack. This may be an important consideration since the Mission Control Agent is given limited permissions to communicate with the Solace Home Cloud.
VPC/VNet isolation is also useful when you keep the event broker services completely separated from your client applications, which provides additional security. You may also want to use VPC/VNet isolation when you want your event broker services isolated in a regional VPC/VNet when you have data sovereignty requirements.
In the following architecture diagram, the red box highlights a Customer-Controlled Cluster.
You can also deploy in the same way in a Dedicated Cluster with a Kubernetes cluster. The reasons to use VPC/VNet isolation are the same - it's just a matter of whether the you or Solace controls the infrastructure where the event broker services are located. The differences are summarized in Customer Roles and Responsibilities for Security.